It’s early July, which means that it’s time for the drive up to Sheffield for SteelCon2018 – The North’s premier Hacker Con. SteelCon is a very friendly, community-minded 6 day conference for hackers and InfoSec people, held at Sheffield Hallam University, in Sheffield. (The main conference is Saturday, recovery on Sunday, and the preceding days are training). This year each batch of tickets sold out within minutes, such is the popularity of this conference, and I was frantically swearing at my phone in the gym when the tickets went on sale at 07:00, whilst constantly regretting not staying at home and assuming that the usually good 4G signal at the gym would be fine. A few minutes of mild panic, and I’d got the tickets.
One of the really admirable things that SteelCon offers, is a series of free training sessions for ticket holders, and held the day before the conference. I was lucky enough to land a spot on “From Zero to Hero: Based on ‘The best TLS training in the world‘ ” with industry expert Scott Helme. Scott (@Scott_Helme) is a security researcher who amongst many other talents is well known for his vocal stance on making the web HTTPS everywhere. ‘The best TLS training in the world’ is a 2 day course where attendees learn and practice the theory of SSL/TLS and Internet PKI. The half day course that I attended was a taster for the 2 day course.
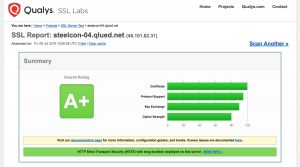
Scott began the course by giving a quick overview of the need for network encryption, before diving into cryptography, keys and certificates, protocols and cipher suites, before letting us loose on our own virtual machines. each machine ran a web site over HTTP, the goal was to follow the tutorial steps to end up with a site running over HTTPS that scored A+ on an SSL Server Test. The course notes were easy to follow, a few typos that I’d made were picked up by Scott, who was always on hand to answer questions and look at any issues we’d run into. After installing a free certificate from Let’s Encrypt, I ran the first SSL test and scored an A; acceptable, but not what we’re aiming for. The final step was to configure the site to run a Content Security Policy (CSP) ‘upgrade-insecure-requests’ that forced all non-HTTPS content over HTTPS. A quick re-run of the SSL Server Test, and my site was running at A+. I really enjoyed this taster, and if my current client obligations and projects allow, I’ll be booking a place on the 2 day course for a deeper understanding of this subject – especially as ‘Zero to Hero’ attendees are offered a generous discount.
On to conference day! There’s always a great buzz walking into SteelCon on conference day; there’s a really good mix of people, and where SteelCon really stands out is that they run kids tracks to encourage young would-be hackers to experiment and learn, so you’ve got seasoned InfoSec attendees with decades of hacking experience mixing with the up and coming hackers of tomorrow, a huge range of people with different skills and abilities in between. SteelCon encourages those without a huge amount of InfoSec experience to attend and meet people, and the whole approach makes for a very chilled and friendly vibe. The laid on breakfast of bacon/sausage rolls and teas also gets people in a good mood 🙂
After the opening speech by Robin Wood (a.k.a DigiNinja), I headed over to Track 2 to see the hugely entertaining Andy Gill (@ZephrFish) give his talk on Breaking into Information Security: Understanding & Helping. Last year I bought his book ‘Breaking into Information Security’, and this talk was about how he came to write the book, the journey he’s made whilst working on it, plenty of anecdotes and stories. Andy had a comprehensive set of slides, but his presentation style is very much a stream of consciousness as well, which makes for plenty of laughs as he launches into his talk. Go buy his book, pay what you can for it and help out a fellow industry bloke who’s forging a really strong presence on the talk circuit. I missed catching Andy at BSides London this year, as it clashed with another talk, so with the knowledge that he’d be at SteelCon, I was really glad of the opportunity to catch his talk.
Next up was a quick walk to listen to Carl Gottlieb (@CarlGottlieb) presenting ‘GDPR for Hackers‘ Carl is essentially, Mr GDPR and if you ever have the chance to see him present, it’s well worth your time; Carl has a wealth of experience in this field, and will drop in countless nuggets of information that you can apply to your own real-world experiences. This talk centred around responsible disclosure, how running the OSINT part of an engagement could cause huge GDPR problems, and addressed a lot of questions and points from the audience. Carl is a great presenter, and can turn what can seem like a very dry subject (GDPR) into one that’s engaging and entertaining.
The next talk was Helen Thakray (@hel_ty), who is a PhD student writing up thesis on social psychology and social identity within hacking communities. Helen’s talk was an interesting insight into how hackers and their community perceive themselves, how being part of a group (or feeling that you’re part of a group) can influence actions and decisions. I found this subject matter an interesting departure from traditional conference subject material, so good job SteelCon for promoting a different take on our community and industry.
SteelCon always put on a good lunch! There’s plenty of it, and it’s not the usual pre-packed nastiness that some events have provided in the past, and back again by very popular demand was the ice cream from Our Cow Molly (@OurCowMolly)
Post lunch I headed over to the main track to catch Neil Lines (@myexploit2600) “The dark arts” I’ve caught a few of Neil’s talks in the past, and find that I’m always very drawn into his talks. This talk was a run through of the processes, tools and approach of a large data breach, and told via the side of the hackers discussing each step, followed by the flip side of Neil being a part of the investigating team who had to forensically analyse the hack and breach. Really interesting stuff and well worth a watch.
Staying in Track 1, Mark Goodwin (@mr_goodwin) took to the stage to present “Fixing revocation: How we failed and how we’ll succeed” Given that I’d spent a morning learning how to deploy TLS certificates, this was a helpful follow up talk, with the history behind a how certificate revocation has problems, being useful, as well as how changes are being made to improve revocation.
After a quick break it was the turn of Chris Pritchard (@ghostie_) to present “How I break into casino, airports and CNI. The basics of SE“. Chris specialises in Social Engineering (SE), and gave us a really engaging and entertaining insight into the experiences he’s had whilst attempting and succeeding to infiltrate buildings, airports, financial institutions, all in the name of testing the physical security of a company. Chris gave us so many really great anecdotes that highlighted the risks that he’s had to take with some engagements (“Armed Police are a physical deterrent in this airport, and even though I had a get-out-of-jail letter in my pocket, I realised that I couldn’t really reach for it as it might get me shot”). Chris imparted a ton of tips that he’s developed over the many physical security testing jobs that he’s undertaken, and perhaps the best piece of advice he gave was one that should be a mantra for us all; Always leave people feeling better for having met you.
Over to the Lightning track now to see what was being discussed, and I happily chanced upon Dirk Wetter (@drwetter) presenting his tool TestSSL. This is a great little tool that I’d not heard of before, it’s a command line tool which checks a server’s service on any port for the support of TLS/SSL ciphers, protocols as well as recent cryptographic flaws and more. Dirk ran a couple of demonstrations of TestSSL in action, and it was interesting to see how deep it analysed, and the potential vulnerabilities that it detected. What was impressive is that he ran it with his laptop tethered to his phone.
I then headed over to the last half of the final talk of the day, “What does it take to steal $81m?” This talk by Donato Capitella (@dcapitella)and Oliver Simonnet (@osimonnet) outlining their research in the security of the SWIFT payment system, and an analysis of some SWIFT related breaches.
There are three tracks that run simultaneously at SteelCon, so there’s no way anyone can attend every talk. Luckily you can watch all the talks over at the SteelCon YouTube channel. Which leads me to a final point about SteelCon; There’s a massive amount of work goes into the AV side of this conference, it’s all managed by Cooper (@ministraitor). On the day, non-attendees can watch live streams of all the talks, and not long after each talk had finished, the AV team had made them available via the YouTube channel. I’ve now got to find time to work my way through all the talks, and appreciate the effort that all presenters went to.
Finally it was the closing speeches to wrap up another SteelCon. This is always very good humoured and a great end to the conference. As ever, the conference made a nice stack of money for the 2 charities that SteelCon supports, there was the usual planning of the after conference party, and the Sunday trip to Laserquest followed by lunch somewhere close by. Contained within the event swag bags were Nerf Guns. Who doesn’t like a Nerf Gun? It seems like everyone at the conference did, with countless spontaneous gunfights kicking off everywhere, which hopefully meant that the LaserQuest games were more hit than miss.
Final word on SteelCon: thanks for the motivational fortune cookies:
Thanks to all those involved with putting on a great SteelCon, looking forward to SteelCon 2019